The Absolutely Craziest Proof Of Concept for an Attack Vector I have ever taught up

While everyone was laughing and joking at the idea of how hilarious the CFP panel must have found it when they pictured it in their heads when reading the brief.
But while everyone was laughing I had the realization which had me just shout out “WAIT, HOLY SHIT, THIS IS POSSIBLE”, which made everyone else laugh even more cause they all realized that my both dangerous and concerning offensive security mind was developing an insane plan for this to be a viable attack vector. So the first thing that popped into my head was to convert the movements into inputs, and how could this be used as an attack vector on a system.
After a few moments of deep thinking, I remember a project using an Xbox Kinect controller, where a project took the input from the IR camera on an Xbox Connect and would then convert that data into an input for the system to recognize, in this case, tv so that a user could change channels with a hand swipe.
Using a package called OpenKinect an open-source library for working with the Xbox Kinect camera. This project could be done easily in multiple languages but would be easiest in Python.
This library can be found here.
https://github.com/OpenKinect/libfreenect
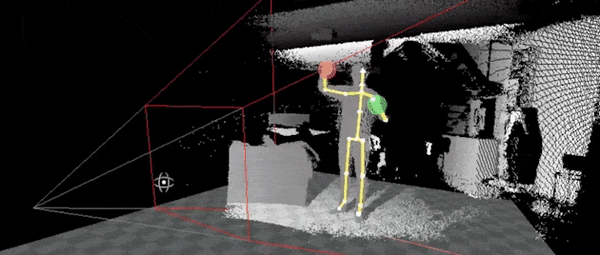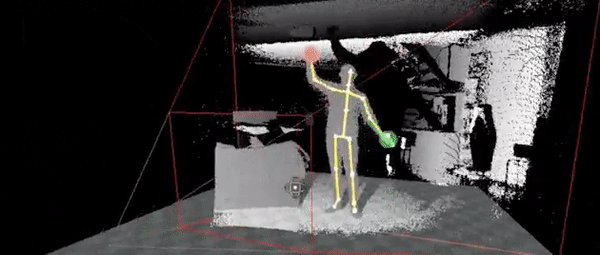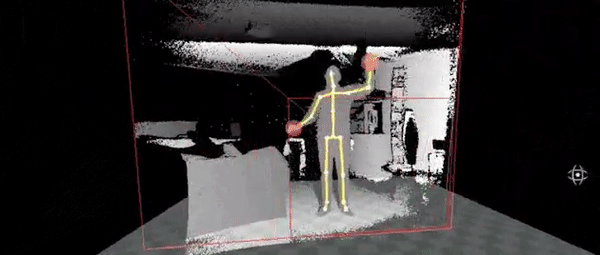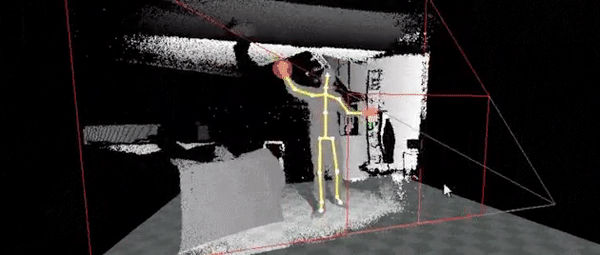
Ok, if this where work, it would require certain movements to either have preset keys or a macro to command outputs.
So now we have a way to interpret the movement now we have to decide on the movements to use and the type of attack.
To keep it simple for demonstration purposes, let’s use a simple attack, an SQLI (SQL Injection), a simple injection 1″=”1″OR”1. This attack basically tells the database to use the first row and line of the database and use it, in many cases this account on that row and location would be the Admin account.
So to do this we no need the movements, for this, we can use simple movements, like the ones you can see on the right

So to perform an SQL injection we would need a precise set of movements that would need to be memorized for it to work. Another option is to have a general set of motions with a tolerance range of being close. This movement input would look something similar to the following movements in sequence on the right side

While I was in TheManyHatsClub voice call one Friday night, one of the other members of the call that goes by Chrissy Morgan was talking about a talk they submitted to Steel Con, an information security conference in the UK called.
This talk idea was “Hacking via Interpretive Dance”, of course, everyone started laughing out loud thinking what a crazy idea, even funnier is the fact that it had been accepted, as it was submitted as a joke.
Morgan’s idea was to have a large group of us get up on the stage and have a mini rave crazy hacker music, covered in LED’s and dancing like Druken idiots for 10 minutes. It would be the last talk of the day before everyone goes out to party, It would have been good fun and probably look something like this the gif on the left (in my mind of course)



Now with the above dance combination, you will have the input of
1″=”1″OR”1 {ENTER}
for those who dont know or skipped to that part, that means use line 1 or database 1 as input. This input is performed by the Xbox Kinect script and setup you now have a full working SQL injection that can be used as an attack and without a keyboard all that is needed are those killer dancing moves youv now learned, the script you wrote, and an IR camera that capable of being scripted with.
The most important part of this attack vector is that it would require a location with an IR camera with scripting capabilities to be exploited, with pre-modification with a working recognition script for this to work, otherwise the attack is dead in the water
These styles of cameras are becoming more common, IR or Terminal Cameras with shell backends used for monitoring the movement of people or deification. With some remote exploitation of that camera possibly through a bad password or ZeroDay exploit, it could be possible to turn these cameras into staging posts, for further exploitation.
An advanced example of this would be:
Exploiting the remote camera, and inserting the modified shell code containing a motion configuration such as a certain type of wave or even characteristics of a CEO walking steps through gait analysis, that would alert or start a form of attack that would only be triggered when that person is in the area or the building.
This could be a simple as launching ransomware, or a complicated attack to gain access to one of their devices