Really a Challenge??
There will be no scripts included in this post, if you are someone who knows about networking, Linux and python you should be easily able to replicate or rebuild the scripts explain in this post. what I will do is for each script I will describe the function of how they work, as I don’t want to enable skids to rebuild or replicate this, mainly due to the fact that this could allow someone to hide data.
So for the first time, I finally got convinced to watch Snowden the film. Yeap, the one from 2016, I had never watched it and was convinced by friends to check it out because it was I quote “there was some cool Shit before he went rouge”. I have always distanced myself from the whole Snowden case and information as I didn’t agree with the whistleblowing as I think many who deal with any form of intelligence, for example, private investigators would have similar opinions keeping such information secret is for the greater good. As for the film, I didn’t enjoy it at all, felt drawn out and boring in attempts to try to glorify what had happened.
There was one scene I had to watch and rewind, re-watched a few times because I thought ok that was interesting, and this was an aptitude test that was given to the recruits at the training facility at 12 minutes and 30 seconds into the film. This was to build a secure communications network from your home city, each candidate is given a home city for example Berlin, Istanbul, New York and so on. The candidates had between 5-8 hours to complete the task.
Below is the clip from the film:
The goals of this test whereas follows:
1 – Build a Covert Communications Network in your home city
2 – Deploy the network
3 – Backup your site (I think they mean site as in location, not a website)
4 – Destroy your site
5 – Restore your site
With the quote “point being to keep your infrastructure up and running securely”.
I talked to a friend of mine who would have insight on a challenge like this, his input was along the lines of more encryption and a few other things required that wasnt listed on the challenge. But that isn’t the challenge so im going to go off exactly what was said in the movie, everything else is fluff that could be added later. I also dont want to use any build scripts made by others, as this feels like cheating although would speed up everything.
So in the scenes that you can see in the movie, there are some commands used by Snowden that can be seen on the screen. These commands that were shown in the seen whereas follows and run as root
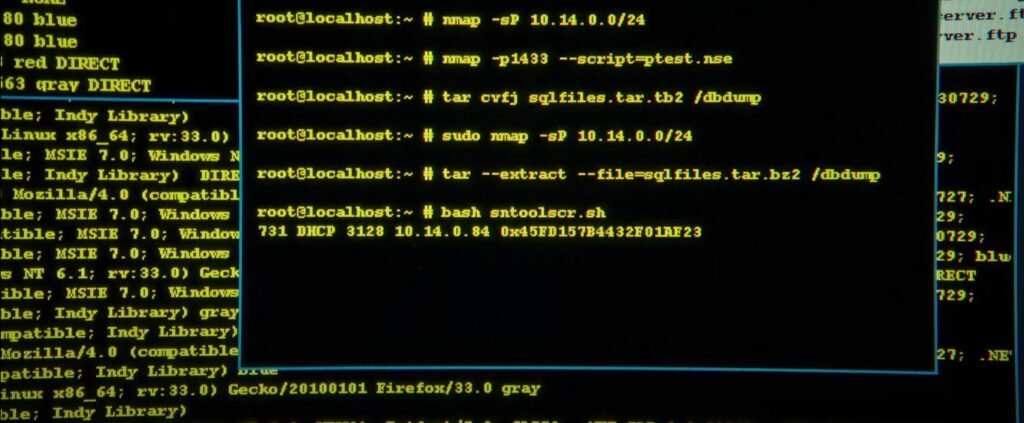
If you’re wondering what these commands do, here is the break down:
- nmap = Network scanning utility
- -sP argument for nmap = default ping scan mode
- -p1433 argument for nmap = the port number 1433 which is a port used by Microsoft MySQL
- –script=ptest.nse argument for nmap = is using the nmap scripting engine, this seems like a custom script to ping sweep based on past input
- sudo = means to run as root although not needed because the user is root already
- tar = program for working with archives on Linux
- ovfj = seemes to be an attempt at providing an argument without
- O = doesn’t seem to be a valid argument only close is –overwrite
- V = show the progress of the archive file also know as Verbose
- F = filename of the archive
- J = Filter archive through bzip2
- –extract –file=sqlfiles.tar.bz2 /dbdump = means to extract this archive know as sqlfiles.tar.bz2 to the directory know as /dbdump
- bash = will read commands from either standard input or a file
- sntoolscr.sh = seems to be a custom shell script to run the whole program
All the while in the background it looks like a packet capture of a Gecko a layout engine developed by Mozilla for firefox.
So now the question is, how would I do this challenge… Well, simply I guess id build a dam secure communications network and not take more than an hour to do it, even as a bad coder with no music playing… The basic idea of what they were doing was to build their version of the TOR network from what I can guess. I will only focus on the basics said by the instructor and not the fact that we can see multiple services that can be seen in the main screen screenshots.
Those services such as an apache website, are as simple as having a build script that runs the service, commands to configure SSL load certificates and move the website and scripts to the right location. These are very simple tasks that I feel aren’t 100% important for this project so I wont, include that information in this writeup.

If you have infrastructure easy day hook each server you have into a switch and just run the commands on each so that its up with each location.
But I dont have the infrastructure, but lets still do it anyway… but of course, doing it the way we are going to is more realistic as it would be similarly done in the real world.
so what we would need is multiple Virtual Proxy Servers each to act as a different city, this is easily done as with digital ocean we can choose VPS’s in different countries and also let’s call my local ubuntu Virtual Machine “my site”.
Im going to use Digital Ocean for ease of use, speed, and most importantly free student credit… if so inclined we could also use AWS, Scaleway, Comtobo, anywhere really that supplies VPS’s services with console access.
So I set up a box in London UK, Frankfurt GER, Toronto CA, Singapore, and New York USA. easily done with a few clicks on the DigitalOcean platform with a running cost of €5 per month on the lowest tier, which is all we need since we are only going to do communications on these.

The reason I decided to use 5 countries and 3 Connections/Hops is that this will give the user 125 possible combinations to the end system, this can easily be scaled up with more boxes and expanding the list of systems to do this.
The next stage is to build a connection to each system, we start by making sure these systems are up to date obviously (this time wasnt counted into overall)
- sudo apt-get update
- sudo apt-get dist-update
- sudo apt-get dist-upgrade
Once this was done the next stage was to lock it down, change default passwords to random character keys (thanks LastPass), and lock down all non-essentials ports for this we can use UFW but since it’s not installed by default we can simply just install it with a few commands.
- sudo apt install ufw
- sudo ufw allow 22
- sudo service ssh start
Next, we need a way to authenticate to the systems with this we can Generate our keys for access with this we will use:
- ssh-keygen -t rsa -m PEM
The above command will generate a key that looks like the following when opened but not redacted
—–BEGIN RSA PRIVATE KEY—–
XXXXXXXXXsdsdsdsdaaffavXXXXXXXXXXXXXXXXXXXX
f9T12ss44ldWF0cXXXXXXXXXXXXXXtbnc2Ewz5yeT2O7yH
EpE+bYXLv7h3U8+gaE2p9I9m6nexHChDFgBcNmXXXXXX
XXXXXXXXXXXXXRSC+fM0+Gk0ZU40awtKKetzPdXXXXX
—–END RSA PRIVATE KEY—–
Copy these keys onto your system “site 1” from each system, to the point you have a folder that looks like this full of pem files. PEM is a container file format often used to store cryptographic keys. It’s used for many different things, as it simply defines the structure and encoding type of the file used to store a bit of data.
PEM files are also used for SSH. If you’ve ever run ssh-keygen to use ssh without a password, your ~/.ssh/id_rsa is a PEM file, just without the extension. Most notably, Amazon Web Services gives you a PEM file containing a private key whenever you create a new instance, and you must use this key to be able to SSH into new EC2 instances.
Basically, you can log into a service such as an SSH session using a .pem file instead of needing to provide a password, both secure and not secure at the same time.
And like that, we are pretty much done on the configuration side the rest is scripting, and in fairness could be done with easily via command line, but we need some superfly 1337 stuff, so lets script that shit out
So how is the command built for usage, we can use the function built-in by default in SSH. To note at this point we never want to be logging in as Root, a custom account should be used. But since this is only for playing around root will do. The account im using is called “secure”, the below command is the test command but we could build off the final script to do it.
ssh secure@[IP ADDRESS 1] -i “\Key_Server_1.pem” -t ssh -i Key_Server_2.pem secure@[IP ADDRESS2]
So the breakdown of this
-i = identitiy file (key file / password file)
-t = execute command on a remote machine this is running the ssh on the remote system
Ok so how do we script this like 1337 tv hackers
- User Chooses destination machine from a given list, for the example lets choose New York
- The script pings all machines to see whos online
- If they responded they are added to list of active systems
- A random selection of 3 machines is done from the list of active systems
- The 3 systems are built into the command with the destination being the 4th in the list
- The script connects and opens up a terminal on the destination machine
- wait for the user to close
Using the script described above the command output would look like this
ssh secure@[London IP] -i “\londonkey.pem” -t ssh -i singaporkey.pem secure@[Singapor IP] -t ssh -i singaporekey.pem secure@[Singapore IP] -t ssh -i frankfurtkey.pem secure@[frankfurt IP] -t ssh -i newyorkkey.pem secure@[NewYork IP]
This command will spawn a console session from Site 1 which is my ubuntu system tunnelling the command through each hop to the final system located in New York.

Connection solved, next step Backup Site
To do this quickly we just tarball our folder we have labelled secrets with a name such as Site1Secrets.tar or [CITY]secrets.tar. Ok, im not going to hold your hand here on how to use SCP, use the man page.
The script would look like
- User Chooses destination machine from a given list, for example lets choose New York
- The script pings all machines to see whos online
- If they responded they are added to the list of active systems
- A random selection of 3 machines is done from the list of active systems
- The 3 systems are built into the command with the destination being the 4th on the list
- Citysecrets.tar is sent to the machine
- Connection ended

The next step, Destroy Site
Easy, we can use the shred function in ubuntu and many other distros, to shred all the files in the folder of course since shred isn’t recursive we would need a script that goes like this
- list all files in the Secrets folder
- Add files to list
- Run shred command on each file in the list
- close
And bang like that we have just destroyed the site

Next Step, Rebuild the Site
Scripting makes this so much easier, all you need is a simple script similar to the original connection one, that connects to a city and downloads the connection keys to your machine for all boxes. If you were a nation-state you wouldn’t connect at all, a good chance it would be a diplomatic courier with a USB key, that contains the connections for a default line of the system that allows you to connect back to HQ and download the keys for every other box. Then once you have those keys you would choose and then connect to the CITY you sent the backup file to download your Citysecrets.tar file and untar it locally while shredding the file on the remote system, using shred.

in conclusion, this took me just over one hour to finish, im a slow coder and needed to research a little. The write up took way longer though than expected, mainly because at the time there was a few beers involved. This was done in the simplest form giving exactly what he asked and no more, that would probably be required, but in fairness as a test, this is a pretty simplistic project.
There are hundreds of ways in which this could be done, I went for the simple ways. I would be interested in hearing other peoples ideas on how they would complete this test.
Another option when it comes to building a secure network is to use software called ProxyChains to forward all TCP traffic over the network, And all this could be automated with a single script in the end to do each section of the test
