A College Project got me Tracking Terrorist on Image Boards


While conduction research for one of my college papers for my Digital Forensics classes on Steganography. I decided to give steganography analysis a go to see how prevalent the found news articles where regarding terrorist organizations using steganography on social media, and have demonstratable information for the paper.
Checking the popular imageboard 4chan, I came across this photo posted by an anonymous user on the Random section also known as /B/ Board of the overall website. The picture was found and stored in a thread about asking for advice about family issues and the original poster was looking for advice on leaving home and starting their life. While looking through the comments, I came across this post that I had to redact as it contained “Not Safe for Work Imagery” in the forum of a nude photograph.
For the thread and conversations that were happening, this photo and comment were very out a context, also checking the poster ID this was the only post from this ID that posted on this conversational thread. The photo was .png and a hash was taken of the file and with some checking around this hash was not found posted or checked in other locations.
Downloading the image in a sandbox and throwing the image trough a tool I downloaded and hosted locally from GitHub, that can be found here.
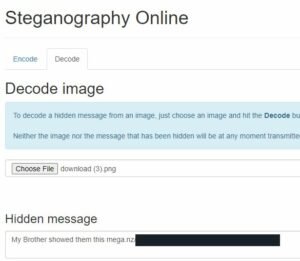
https://stylesuxx.github.io/steganography/
I was able to pull information from the photo, it had the following text inside the image “My Brother showed them this {mega.nz link}
Researching this tool more, since it is an Open Source tool it would not be useable in court in many cases as I was unable to find any use cases that may have set a precedent for the tool to be used in forensic evidence collection.

Unfortunately, due to time limitations and legal limitations that would give more information such as IP Addresses and possible accurate location data, I was unable to do any more during this investigation.
The findings were submitted to the appropriate authorities for further investigation, in this case, it was via the Federal Bureau of Investigation to their Counter-Terrorism Center. There was no follow up after the investigation from the FBI so it is unknown the current stats of this evidence. Before someone says about publishing evidence it has been over a year from the submission of this Intelligence to the posting of the information, and the video has long since been taken offline.
